Cybersecurity in PSAPs – More security through the separation of networks
- December 5, 2023
- Categories: Cybersecurity
The risk of becoming a victim of a cyber attack is increasing, and PSAPs are also affected. The impact such an incident has on the operational readiness of the PSAP can vary greatly. In the best case, only non-critical systems are affected. In the worst case, the control centre can no longer accept emergency calls or alert emergency services and people can be harmed.
In order to keep the damage in the event of an attack to a minimum, it is important that the attackers can only penetrate a small area of the network, and preferably a non-critical part. So that the attackers cannot spread into critical areas or even the entire network, it is important to separate the networks in a PSAP.
This blogpost is intended to help minimize the impact of a cyber attack. First, the process of a typical attack is shown. We then explain what the separation of networks means in theory. Finally, concrete practical measures are shown on how networks can be separated sensibly.
Process of a typical attack
In most cases, attacks take place via the Internet. The attackers usually choose targets that they can penetrate easily and undetected. These are usually destinations that can be reached online. Of course, it is also possible to attempt a local attack, but the effort involved is significantly greater and the risk of the attacker being caught is very high. Since almost all companies, authorities, organizations and PSAPs must be accessible online in order to carry out their work, an attack via the Internet is the route that causes the least amount of effort and has a low risk of criminal prosecution for the attacker.
An attack often begins with an infectious email. This can either exploit a security vulnerability in the recipient’s email client or have a malicious attachment that the recipient accidentally executes. Further information on how to increase the security of email traffic can be found in the blog post Cybersecurity in PSAPs – the Danger of Malicious E-mails.
Other ways to break into a system include unsecured remote access, for example via the widely used Remote Desktop Protocol (RDP). If the RDP server is not up to date, attackers can connect to the server by exploiting security vulnerabilities. The attackers could also have previously obtained credentials via a phishing attack and used them to log in to the target server like a regular user.
Another attack vector is the exploitation of vulnerabilities, for example in the web browser. If a user visits an infected website, it is possible that malware is installed in the background on the user’s client. The risk of this increases if security updates are not installed in the web browser. Visiting seemingly secure websites from other authorities or well-known organizations also poses a risk: Nobody can rule out that their websites have also fallen victim to a cyber-attack unnoticed and are now spreading the malware themselves.
We will now assume that a user’s client in the PSAP was infected by malware via one of the methods described. The attacker will try to expand his rights and spread throughout the network. If necessary, the attacker will now download additional malware. He will then attempt to break into additional systems from the controlled client. In order to cause as much damage as possible or to blackmail the PSAP with ransom demands, the attackers’ goal is to gain control over the most critical system possible. This can be, for example, a central directory service (Active Directory), the CAD or the server required for communication (ICCS), emergency calls, etc. These systems usually do not have direct Internet access. IP-Telephone systems, for example, are usually protected from the Internet by a session border controller. Since the attacker already controls a client in the control centre network, these systems are now also at risk since it can now be attacked from within.
In order to break into these critical systems, he can exploit security gaps or use previously captured credentials. Since the attacker comes from the internal network, the attacker usually has a much larger choice of exploiting security gaps, as the services on the systems are often only shielded from the outside. You can imagine it like an attack on a castle. After the castle walls and protective moats have been overcome with great effort, it is significantly easier to open the doors of the buildings within the castle. More on this later. In the worst case, the attacker can extend his control to all of the PSAP’s systems. Depending on the motive, data can now be spied out or services can be prevented or manipulated.
Networks and separation in a PSAP
A network consists of different clients and servers. So that they can communicate with each other, they provide services that can be accessed via the network by another client or server. It is sufficient for this that the communication partner is in the same network. Local networks are separated from the Internet by a firewall or router. Systems in the local network can only be reached from the Internet if the firewall allows this. However, within the local network, all systems can communicate with each other. Remember the example above with the castle. The local systems are located inside the castle walls.
For the reasons mentioned above, the local network should also be divided into different segments. For example, not every system needs Internet access, or there may be services that need to be accessible from the Internet and others not. In the simplest variant, systems that must be accessible from the Internet (e.g., web services) are moved to their own network, and all other systems (internal systems) to another. See the following figure:
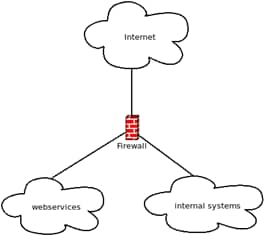
Users whose clients are in the internal systems can now only communicate with each other. If they want to access the web services, the firewall must allow this. The other way around, access from the web services to the internal systems is generally prohibited by the firewall. If the web services are accessible from the Internet and are brought under control by an attacker, it is no longer possible for the attacker to extend his control to the systems in the internal system. This is just a very simple example. In practice, a PSAP should segment the networks into much smaller pieces.
In the next figure, PSAP systems are taken as an example. There is a network in which the CAD and ICCS servers are located and a network for the associated clients. Another network is intended for systems that require access to the Internet. For example, for processing emails or accessing websites. In the example, only a simple firewall protects the network because it is easier to understand. In a real system, a control center should install at least a second firewall in order to provide even better protection for critical systems such as CAD and ICCS. Ideally, the firewalls are from different manufacturers as firewalls can also have security gaps.
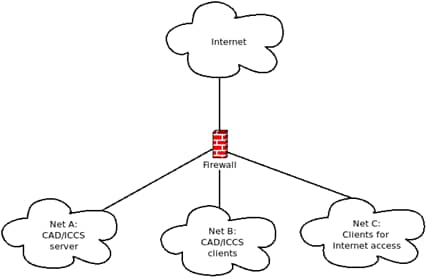
For example, if a client in Net C becomes infected with malware due to a malicious email, the firewall prevents the problem from spreading to the critical systems in Net A and B. Of course, an infection in Net C is also annoying and can affect the work of the PSAP. However, emergency calls can still be processed and emergency services alerted.
In the next example, the PSAP is expanded to include additional networks. For example, system engineers can access the servers in Net A via remote desktop connections. To do this, they use clients in the newly added Net D. Since PSAP wants to provide WLAN for guests, another separate network is created for them. After all, guests should not access the PSAP systems with their own devices but should only use the Internet:

The more the networks are separated from each other, the more difficult it is for an attacker to spread through the PSAP network. In extreme cases, each host is on its own network. In practice, of course, this involves a lot of effort, which is why compromises are usually found and different hosts of a category are combined in one network. In the next section we will find out which tools can be used to practically implement network separation.
Protective measures to implement network separation
One of the most important components in separating networks are firewalls. The firewalls control access, which network traffic is allowed between different networks and which is denied. When configuring the firewall, the principle that must always be observed is that all network traffic is initially denied. Only connections that are absolutely necessary for the operation of the PSAP are allowed. It is also important that not every service can be accessed across network boundaries. Here again, only those services that are absolutely necessary are allowed. For example, if a server requires access to a remote web service via HTTPS, FTP is still denied. This makes it more difficult to download malware from the Internet. These regulations also apply in the internal network. Strict policies prevent security vulnerabilities from being exploited in services that do not necessarily need to be accessed.
The actual practical separation of the networks can be done in different ways: In the most understandable variant, separate network cables are simply used for each network. So the networks are physically separated. The big advantage is the high level of security that is achieved. The disadvantage is the high effort, especially over long distances across several rooms.
Another variant is the use of a Virtual Local Area Network (VLAN). With VLAN it is possible to separate multiple networks and still run them over a single network cable. The separation is purely virtual. To use VLAN, a switch that supports the technology is required. This is the rule for professional switches that are commonly used in control centers. The advantage of VLAN compared to physical separation is the significantly lower effort. The disadvantage is the slightly lower level of security. For example, if an attacker has taken control of a switch, he can manipulate the VLANs. In the event of a physical network separation, the person would have to be present in person.
Conclusion
Connections to and from the Internet are now mandatory in a PSAP. Like all authorities, companies and organizations, PSAPs also work with information from the Internet, communicate via email or use interfaces to remotely provided services. The emergency calls alone, which are now transmitted to the PSAP via VoIP, prevent the PSAP from being completely separated from the Internet.
This naturally increases the risk of becoming a victim of a cyber attack. But there are ways to secure the PSAP. If an incident does occur, it is important to keep the impact as low as possible. This is possible by cleverly separating the networks in the PSAP.
Separating networks does not make a PSAP invulnerable, but it increases the chance of being able to continue to operate the most critical systems in the event of a security incident. This is important in a PSAP.

Henning Schmidtpott
- Henning Schmidtpott#molongui-disabled-link
Share this blog post on:
